The definition of proxy is a substitute. A proxy server, or simply “proxy,” addresses a common issue experienced by everyone who uses the internet.

Img source: carneyco.com
Contents
The Problem
A user’s IP address – your IP address, is made available to the websites that you visit. And, in order to be online, you will have to have an IP address. As a result, there is no way to avoid having an IP address and therefore avoid being identified.
To be clear, the computer that you use is assigned the IP address. Of course, more often than not, you will be the user.
Since each computer must have one, what you can do to protect your privacy is assign another IP address to your computer. Your true identity will remain concealed from the web public.
Some people live by the adage “Ignorance is Bliss” and are therefore unperturbed by the possibilities of their IP addresses being identified. The way that people use this information can range from mildly irritating to dangerous.
Sharing a computer’s IP address is a necessity to have an online presence but sharing your true address is optional.
Img source: sales-marketing-seo.The Solution
Proxy servers and VPNs let you browse the internet under a different IP address.
There are several types of proxies and VPNs from which you can choose. Their differences lie in what they can do, how they do it, and in their price. The main aim of each is the same – assigning a different IP address for your computer from what was provided by your internet service provider.
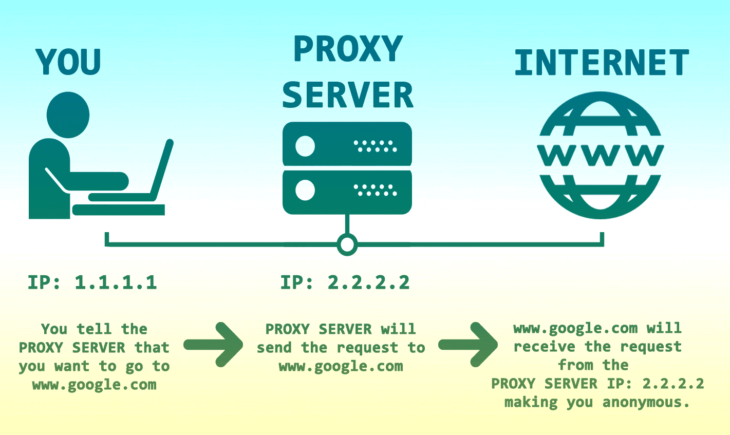
Img source: stupidproxy.com
Proxies
A proxy server acts on behalf of your computer and communicates with websites for you.
Proxies were originally used by businesses to prevent IP addresses from conflicting with one another when multiple computers were connected to the internet. They were a necessity to be able to be connected to the internet.
They are now used by businesses for improved performance. Proxies enable squid caching – the temporary storage of frequently used online files and downloads. It allows quick access to this information by multiple users because they don’t have to download it individually and take up a lot of time in the process.
Proxies also contribute to security for businesses. When they are used in conjunction with tunneling protocols, they verify data that is coming into a business’ network and encrypt anything that is going out. They protect the business and customer information.
Like businesses, individuals employ the use of proxies to protect their personal information as well. A proxy helps you to maintain your privacy as you enjoy the use of the internet. Now, enjoyment is one thing, but modern-day life demands that you use the internet for serious purposes as well. So, there is no avoiding its use. A proxy can effectively protect you as you go about doing your necessary activities online.
Another way in which you can use a proxy to maintain your anonymity arises because of “geo-blocking.” Geo-blocking is the term used for the restrictions imposed on the IP addresses of certain countries or geographical areas. Proxies make it appear as though you are elsewhere and allow you to get access to that restricted content. Censorship restrictions can also be successfully skirted by using a proxy.
Img source: pixfeeds.comTypes of Proxies
Forward proxies send outgoing requests from a private network or intranet to the internet.
A reverse proxy checks the information coming into a private network from the internet. It is used for protection and security of the server. It involves tasks like caching, authentication and decryption.
Other types of proxies are as follows:
- Transparent proxies are positioned between your computer and the internet. It may be used for content filtering.
- Anonymous proxies identify themselves as proxies but don’t share your IP address with the website.
- Distorting proxies communicate to a website that it is a proxy and shares an incorrect IP address for you.
- High Anonymity proxies protect your true IP address by ensuring that it remains concealed.

Img source: youtube.com
Shortcomings of Proxies
Although they aim to achieve certain goals for you, there are degrees to which proxies are successful in achieving them. Nefarious individuals and groups work incessantly to undermine the successes of proxies, their operators and developers. Law enforcement agencies and governments also try to impose laws and clarify definitions of morality and legality with respect to privacy and security. As such, the discussions and the development of proxies are fluid topics. The same can be said of VPNs.
Here are some ways in which proxies are not perfect:
- Performance – the speed of your browsing experience may be affected. Although it may not be a significant slow down in performance, there is a compromise on speed. Your streaming experience, for example, may be significantly affected but the effect on other activities for which you would use a proxy can be negligible.
- Your browsing activities may be logged – a record of your browsing history may be made and stored by the proxy server.
- It can be expensive – free proxies are also available, but these tend not to be as secure as you would need them to be. However, there is a wide number of choices for users.

Img source: cnet.com
VPN
VPN stands for Virtual Private Network. VPNs also address the problem that was stated above. They maintain your anonymity and provide you with a certain level of security. This is done through tunneling and encryption. Tunneling is a set of rules that allows your data to be moved securely from one network to another. Encryption is the process of making the information unreadable to unauthorized users.
You have a number of different choices which come with their own set of benefits and shortcomings.

Img source: valuewalk.com
Types of VPN:
The different types of VPNs available to you are really the different types of protocols.
- PPTP – Point to Point Tunneling Protocol was the first one to be developed. It is fast, easy to use and can operate on multiple platforms. However, security proved to be vulnerable. Later protocols addressed those issues.
- L2TP/IP sec – Layer Two Tunneling Internet Protocol Security is compatible with IOS. It is secure and provides 256-bit encryption. The main drawback is that it is slow.
- SSTP – Secure Socket Tunneling Protocol was introduced by Microsoft. It provides good security and can get through most firewalls. However, it is widely considered to be a Windows only platform.
- Open VPN – this is the newest and most advanced VPN. It can be configured to work on most platforms, and it is continually updated. It is the fastest and most secure protocol. However, it is not as easy to set up as some of the other protocols.

Img source: youtube.com
Shortcomings of VPNs:
- Expensive – Effective VPNs that function well and are reliable can be costly. However, free VPNs can cost you in another way. Since they are offered to the public for free, they must earn money in another way. Ironically, some free VPN service providers might end up selling your browsing activity to ad companies who will happily solicit you.
- Slow speeds – the encryption and encapsulation process can result in very slow and irritating speeds for you. You will have to decide whether or not this is acceptable since this is the price that you may have to pay for anonymity and security. Conversely, in order to solve this, the price of better speed would be a paid VPN.
- Complexity – some VPNs can be complicated and may even call for an intimate knowledge of network security if you would like them to function optimally. This can eliminate a substantial portion of the users who would like to ramp up their online security. Luckily, there are numerous other choices of VPNs or users may opt for proxy servers to fulfill their security needs.

Img source: technotification.com
You can effectively use VPNs and proxies together in order to get the best out of both of these tools. Different actions can be performed optimally with each, and since they both have on and off switches, one can carry out its task without a hindrance from the other.
Apart from the choice of the types of proxies and VPNs, your other decision can be on the brand.
Whatever you choose, proxy or VPN, it should be able to fulfill your purpose. The one with the best capabilities may not be the most optimal one for you. Of course, more capabilities and greater functionality would mean a higher price. In other words, it is not necessary to pay a higher price for something that will not be used fully.
The main thing is that you are protected from the possible dangers that lurk around because of Internet usage. However, being online is no longer a luxury. It is now a utility. Your education about it is therefore necessary. It is also arguable that proxies and VPNs for your private use will also become a necessity in the future. People who wish to capture your personal information for their entertainment and personal gain have ensured that.
Proxies and VPNs will continue to develop as well and will compete with each other as they grow. But, as long as privacy and security remain threats, they will undoubtedly continue to complete each other.
